Too many tools. Too many alerts. Not enough clarity.
If you are part of a SOC, a CSIRT team, or a threat hunting unit, you have felt the pressure. Incidents stack up. Logs pile in. And you are left stitching together disconnected signals across endpoints, users, and workloads, often without the full story. That is exactly where Cortex XSIAM steps in, and why this Cortex XSIAM Investigation and Analysis course exists.
This course is designed for cybersecurity professionals who specialize in incident response. It teaches you how to use XSIAM to investigate threats faster, make sense of the chaos, and take action backed by evidence, not hunches.
Delivered by Datacipher Education Services, an Authorized Palo Alto Networks Training Partner, the program combines expert-led sessions with hands-on labs tailored to address real-world SOC challenges.
In this guide, you’ll find everything you need to know: from who the course is for, to what you’ll learn, and how it levels up your response game.
Why Take the Cortex XSIAM Investigation and Analysis Course?
SOC and incident response teams are under constant pressure to triage, investigate, and act faster than ever. But traditional tools and disconnected data often slow them down. Cortex XSIAM is designed to change that, and this course gives you the skills to use it effectively from day one.
Here’s how this training helps you grow:
#1. Build deep investigation skills across endpoints, logs, and alerts
Learn to analyze key assets, artifacts, and event sequences using XSIAM. Gain hands-on experience with causality chains, threat intelligence, and incident handling.
#2. Get confident with XQL and advanced SOC workflows
Master XSIAM Query Language (XQL) to extract meaningful insights from large volumes of security data. Use automation and dashboards to streamline your response.
#3. Grow your credibility as a modern SOC analyst or responder
By learning how to operationalize Cortex XSIAM, you position yourself as a forward-looking security expert who can handle advanced, high-volume investigations.
#4. Expand your opportunities with MSSPs and consulting roles
Whether you’re working in-house or with a service delivery partner, this course equips you with real-world skills that are valued in global SOC and MDR environments.
#5. Prepare for the Palo Alto Networks XSIAM Analyst Certification
This course aligns with the objectives of the XSIAM Analyst Certification, providing you with the hands-on skills and platform knowledge needed to deploy, operate, and investigate incidents using Cortex XSIAM. You can find the exam details here.
Want a sneak peek before you dive in? If you’d rather watch than scroll, this short video walks you through everything about the Cortex XSIAM Investigation and Analysis course. From the key skills you’ll gain to the roles it supports, this preview gives you a clear sense of what to expect and how it can advance your career. Watch now to see if this course is the right fit for you.
Cortex XSIAM Investigation and Analysis Course Overview
The Cortex XSIAM Investigation and Analysis course is a two-day instructor-led program designed to equip cybersecurity professionals with the skills to investigate incidents, analyze artifacts, and use automation effectively within the Cortex XSIAM platform.
This course blends expert-led lectures with immersive hands-on labs, enabling learners to build real-world investigation and response capabilities across diverse SOC environments.
| Feature | Details |
| Course Duration | 2 days |
| Delivery Format | Instructor-led training with hands-on labs |
| Course Level | Intermediate |
| Target Audience | SOC analysts, CSIRT/CERT members, MSSPs, security consultants, system integrators |
| Prerequisites | Foundational cybersecurity knowledge; experience with incident analysis and investigation tools |
| Training Credits | 40 |
| Course Fees | INR 40,000 or USD 1,500 |
Target Audience
The Cortex XSIAM Investigation and Analysis course is designed for cybersecurity professionals involved in threat investigation, incident response, and SOC operations. It is ideal for:
- SOC, CERT, CSIRT, and XSIAM Analysts and Managers
- MSSPs and Service Delivery Partners
- Internal and External Professional Services Consultants
- Sales Engineers working in security environments
- Incident Responders and Threat Hunters
This course is best suited for those looking to operationalize Cortex XSIAM within complex, multi-source security environments.
When this Palo Alto course feels close but not quite right, filling the form below can help you make a clearer choice.
Prerequisites
To get the most value from this course, participants should meet the following prerequisites:
- Foundational understanding of cybersecurity principles
- Experience with incident analysis and threat investigation
- Familiarity with using security tools in SOC workflows
These prerequisites ensure that learners can effectively engage with the course content and hands-on labs without requiring foundational instruction.
What Does the Cortex XSIAM Investigation and Analysis Course Cover?
The Cortex XSIAM Investigation and Analysis course is designed to build hands-on expertise in incident investigation, alert correlation, and asset analysis using Palo Alto Networks’ XSIAM platform. Focused on real-world SOC operations, this course equips learners to streamline detection, accelerate response, and uncover root causes with precision. Each module builds your ability to navigate incidents end-to-end using automation, threat intelligence, and XQL-driven analytics.
The key modules covered in this course are:
- Introduction to Cortex XSIAM
- Endpoints
- XQL (XSIAM Query Language)
- Alerting and Detection
- Threat Intel Management
- Automation
- Attack Surface Management
- Incident Handling
- Dashboards and Reports
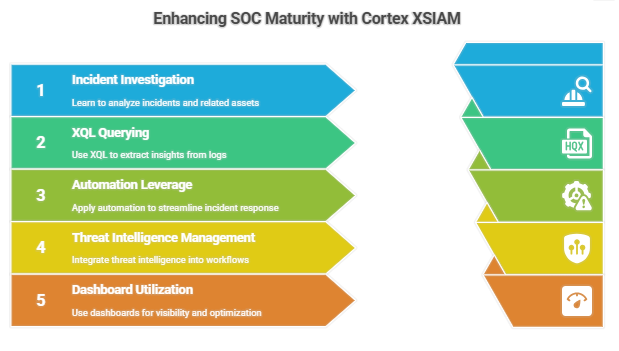
By the end of this course, you will be able to:
a. Investigate incidents and analyze related assets, alerts, and artifacts using XSIAM’s visual investigation tools.
b. Use XQL to query logs, extract meaningful insights, and support rapid decision-making.
c. Leverage automation to reduce manual workloads and improve consistency in incident response.
d. Manage threat intelligence and integrate it with alerting and detection workflows.
e. Use dashboards and reports for visibility, performance tracking, and SOC optimization.
Additional key outcomes include understanding attack surface management, applying causality chains during investigations, and using Cortex XSIAM to enhance overall SOC maturity. This course prepares you to confidently operate within high-volume, hybrid environments using one of the industry’s most advanced security operations platforms.
Next Steps
After completing the Cortex XSIAM Investigation and Analysis course, your next step is to pursue the Palo Alto Networks Cortex XSIAM Analyst Certification. This certification validates your ability to investigate, operate, and analyze incidents using the XSIAM platform in real-world SOC environments.
Enrolling in the Cortex XSIAM Investigation and Analysis Course
The Cortex XSIAM Investigation and Analysis course is a two-day, instructor-led training offered through Palo Alto Networks’ network of Authorized Training Partners (ATPs), including Datacipher Education Services. The course is available in both online and classroom formats, providing flexibility to match your learning style and location.
How to register for the course?
#1. Visit the official Palo Alto Networks training portal and search for the Cortex XSIAM Investigation and Analysis course under the instructor-led training section.
Source: Palo Alto Networks
#2. Use filters to refine available sessions by:
- Region: Choose a location that aligns with your time zone
- Language: Pick your preferred training language
- Time Zone: Select sessions that fit your daily schedule
#3. Choose an Authorized Training Partner like Datacipher, or register directly through the partner’s website.
#4. Complete the enrollment and payment steps to confirm your seat. Some sessions are marked as guaranteed to run, offering added assurance even with limited enrollments.
Datacipher Education Services is a recognized Palo Alto Networks Authorized Training Partner, trusted by enterprises throughout the APAC region. Our expert instructors combine real-world SOC experience with platform expertise to ensure that each session is highly practical and relevant.
To register through Datacipher, select “Datacipher” from the list of ATPs during registration, or go directly to our course page to enroll.
Training Credits
The Cortex XSIAM Investigation and Analysis course is eligible for training credits under the Palo Alto Networks training program. Organizations can purchase training credits in advance, each valued at $100, to access this and other authorized Palo Alto Networks training offerings.
This course requires 40 training credits, which is equivalent to $4,000 (excluding GST). These credits remain valid for 12 months from the date of purchase and can be redeemed through any ATP, including Datacipher.
If your organization is planning for continuous upskilling, using training credits is a smart way to streamline budgeting and gain access to multiple courses across the Palo Alto Networks curriculum. For full details on training credits, read this datasheet and program guide.
Become a Cortex XSIAM Expert with Datacipher Education Services
Source: Datacipher
Investigating advanced threats, analyzing incidents, and reducing alert fatigue takes more than product knowledge; it demands platform mastery and operational insight. That’s why SOC teams across the APAC region turn to Datacipher Education Services to go beyond the basics and lead with confidence on Cortex XSIAM.
As a Palo Alto Networks Authorized Training Partner, Datacipher delivers focused, hands-on instruction that prepares you to deploy, operate, and analyze security incidents using Cortex XSIAM in live SOC environments. Our training is trusted by enterprises like IBM, Hitachi and Sony, and is built to deliver maximum real-world value.
What makes Datacipher training different?
- Certified instructors with real-world experience managing and investigating incidents using Cortex XSIAM
- Lab environments that replicate enterprise-scale SOC workflows and threat scenarios
- Flexible scheduling with both virtual and in-person formats available every quarter across APAC
- Personalized support from course registration through post-training application
- Curriculum focused on applied investigation, not just feature walkthroughs.
Recently, one learner shared:
“The Cortex XSIAM training by Datacipher bridged the gap between theory and practice. I now handle investigations more confidently at HCL.”
— Rohit Varma, HCL Technologies
If you’re ready to level up from basic analysis to deep, end-to-end incident investigation, Datacipher Education Services is the training partner that brings Cortex XSIAM to life.
Frequently Asked Questions
1. What is Cortex XSIAM and how does it differ from traditional SIEM solutions?
Cortex XSIAM is Palo Alto Networks’ next-gen SOC platform that unifies SIEM, SOAR, and XDR capabilities. It’s built to automate alert correlation, asset context, and incident response using machine learning. Unlike traditional SIEMs, it’s designed for cloud-scale analytics and real-time investigation. This results in faster, smarter, and more autonomous security operations.
2. How does Cortex XSIAM integrate threat intelligence into alert detection and handling?
XSIAM consolidates global and local threat intel feeds to enrich alerts in real time. It maps indicators of compromise (IOCs) against ingested data for faster detection. This intelligence directly informs alert scoring, prioritization, and automated response actions. Analysts can also drill into threat details to investigate the full scope of an incident.
3. What role does automation play in Cortex XSIAM’s incident response workflow?
Automation in XSIAM reduces manual investigation tasks by triggering predefined playbooks. It helps correlate alerts, enrich data, and even initiate response actions without human delay. This boosts consistency, reduces alert fatigue, and accelerates time to resolution. SOC teams can focus on high-value analysis instead of repetitive triage.
4. How does this course support career growth in modern SOC and incident response teams?
The course equips you with hands-on XSIAM skills that are in demand across advanced SOCs. You’ll learn how to handle real-world incidents using XQL, threat intel, and automation. It positions you for roles like XSIAM analyst, SOC responder, or detection engineer. Mastering XSIAM adds serious value in MSSPs, global enterprises, and consulting roles.




